
In a digitally-driven world, every individual and organization communicates through the internet and shares their confidential information. And to ensure secure data transmission, some high-end cybersecurity firms consistently work on the backend.
Everything getting online provides various benefits; however, it also attracts malicious actors whose primary purpose is breaching data.
In 2022, the main organizational objectives are ensuring data integrity, confidentiality, and availability. And to achieve them, understanding top cyber security trends is necessary.
By reading further, you will learn about the security approaches, attacks, and mechanisms in trends, affecting the day-to-day tasks.
Table of Contents
Cyber Security Trends To Look For:
Strengthening Of Remote-Work Security:
During the first phase of Covid-19, every company faced the consequences of global lockdown. Due to this, all the businesses get adversely affected, leading to the remote-working culture.
At first, the employees were using their own devices without any VPN and appropriate security measures, increasing the probability of data breach. In 2022, remote working culture has become routine, and organizations are building relevant standards to protect data transactions.
Currently, whether it’s personal devices or the company’s assets, the person doesn’t get access to resources until successful authorization. In addition, every employee has to connect to the organizational network through a Virtual Private Network to prevent data and bandwidth throttling.
Integration Of Artificial Intelligence:
Artificial Intelligence is becoming a primary technology in every domain to accelerate business growth.
In cyber-security, AI aids professionals in configuring a robust security mechanism, which can automatically detect and mitigate attacks. Moreover, AI holds the capability to learn about cyber-attack behaviour and generate a mitigation plan by integrating with Machine Learning modules.
Moreover, it is crucial in tightening overall security and decreasing the data breach probability.
Hence, organizations are utilizing Artificial Intelligence for detecting frauds, streamlining security operations, for monitoring network and internal communications. Every industry is adapting AI-based hardware and software tools in 2022, whether it’s an IT company, telecommunications, banking, or supply chain.
Cloud-Based Vulnerabilities:
Due to high performance, scalability, and reliability, Cloud as Backend is becoming preferable for most organizations. It also leads attackers to investigate cloud infrastructures and discover potential loopholes.
Although vendors such as Amazon Web Services, Google Cloud, and Microsoft Azure ensure data integrity, confidentiality, and availability, there are still chances of unauthorized access to cloud resources.
Furthermore, keyloggers, Insecure APIs, Buffer Overflow, and lack of security on physical machines are top vulnerabilities you must take care of in 2022. Otherwise, an attacker can hijack accounts, utilize data for personal purposes and target your business for ransom.
In addition, there is a 68% chance of cloud infrastructure getting hacked due to a lack of relevant security measures in 2022.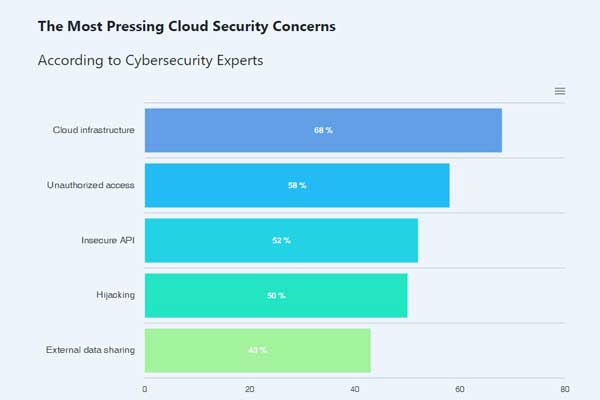
Growth Of Ransomware
Cyber-security experts have been dealing with Ransomware attacks for a long time, and several pieces of research get performed yearly to prevent it.
In recent two years, attackers are mostly performing it on high-profile businesses. But, small-scale organizations have the same probability of getting hit by it. In 2022, attackers will have access to various tools, aiding them in creating new ransomware variants in a shorter timeline.
As per the reports of ransomware.com, only 16% of firms are less likely to be targets of a ransomware attack.
In addition, cyber-criminals also started providing ransomware-as-a-service to earn high income from unlawful activities. Hence, security experts advise every organization to build mitigation and recovery plans for seamless working in 2022.
Political Cyber-Wars
Cyber warfare is becoming a common issue, whether it’s a conflict between two countries, national organizations, or political parties.
Organizations hire hackers and pay them a hefty amount to breach competitors’ systems to corrupt or disclose their confidential information. Such operations have been active from past many years. However, these are getting highlighted with more internet and digital device utilization.
Everyone is aligning their policies and processes to the latest ISO, NIST, ISMS, and SANS Security Policy resources, from government-sponsored to private institutions. It will help them improve resilience and prevent attacks on primary and secondary assets.
Attacks On IoT Devices
By 2020, you must have seen smart devices installed everywhere, from offices to colleges and even on public transport.
All these devices connect to the internet to establish links with the primary server and database. Attackers try to take unauthorized access to these devices to enter the network and exploit backend services.
Moreover, cyber-criminals are discovering IoT device vulnerabilities to connect them to a bot network for executing Denial of Service attacks.
With the heavy adoption of IoT devices in 2022, organizations are increasing the chances of cyber-attacks, leading them to pay hefty amounts in return. Firms must update their policies and establish an encrypted communication channel between devices to prevent it.
The Demand For Cyber-Security Professionals
With the rapidly increasing attacks across small, medium, and large-scale organizations, the demand for security professionals is skyrocketing.
Maintaining the security of an enterprise is a complex and time-consuming task. And many experts are resigning from their jobs due to stress and burnout. Besides this, new startups launching are also a primary reason for the demand for security engineers.
According to Cybersecurity Ventures, there will be more than two million vacant positions in this domain by 2025.
Moreover, in 2022, companies are ready to pay more than average to security experts for filling positions. In the upcoming months, the demand will increase as global conflicts emerge, leading to cyber-wars.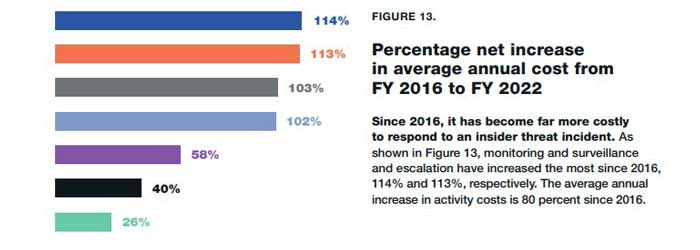
Threats From Inside
Not every attack gets executed by someone outside of your organization; its source can also be anyone present inside the company premises.
Its primary reasons are clicking on phishing mail, providing access to third-party websites, sharing details with unauthorized persons, and downloading malicious files. In 2022, insider threats are becoming very common in each industry.
And to mitigate them, enterprises are moving to configure access controls, authentication, and authorization mechanisms. In addition, the requirement of physical controls is also accelerating to control the access to the comms room.
Additionally, companies provide cyber-security training to all current and new joiners to make the ecosystem safe and secure from internal and external threats.
2021 Cost of Insider Threats Global Report
According to the Ponemon report, the cost of insider threats increased by 114% from 2016. and is expected to grow more until the end of 2022.
Attacks On Automobiles
With the launch of internet-connected smart vehicles, automobile customers face data breaches. In some cases, people are losing control of their cars and cannot unlock them.
In addition, the feature of connecting mobile with the car’s Bluetooth also puts the device at risk.
In 2022, the cases of eavesdropping hacking into the vehicle network are rapidly boosting. And to prevent them, automobile enterprises collaborate with IT firms to craft a secure automotive system.
Concluding Up
Cyber-security domain has seen immense growth in 2022. Whether it’s a cyber-attack, a mitigation strategy, or the advancement of a tool, all are getting modernized.
In addition, ransomware attacks are getting more powerful, and cybercriminals are providing hacking services. In addition, automobiles are also the target, along with IoT devices in colleges, hospitals, and government sectors.
Although enterprises are filling all the vacant security engineer positions, the demand for professionals will still increase.

 About the Author:Jemin Desai is a Technical Product Manager and tech-savvy at Positiwise Software Pvt Ltd,
About the Author:Jemin Desai is a Technical Product Manager and tech-savvy at Positiwise Software Pvt Ltd, 















Thanks for sharing such an amazing content, Very nice article.
Welcome here and thanks for reading our article and sharing your view. This will be very helpful to us to let us motivate to provide you with more awesome and valuable content from a different mind. Thanks again.